What Is Penetration Testing and Why Is It Important?

Cybersecurity is a minefield of constantly evolving threats. Statistics show a staggering increase in cyberattacks, with a report by Cybersecurity Ventures predicting that cybercrime will cost the world $10.5 trillion annually by 2025. This escalation underscores a critical need for rigorous security measures.
In analyzing security breaches, it’s observed that most incidents exploit existing vulnerabilities, many of which could be preemptively identified through penetration tests (pen tests). The 2020 Verizon Data Breach Investigations Report highlighted that over 70% of breaches were caused by vulnerabilities that penetration testing could have potentially uncovered.
These trends and figures emphasize the criticality of penetration testing services as a strategic component in a business’s cybersecurity arsenal. It not only identifies and addresses vulnerabilities but also prepares organizations to respond effectively to the dynamic nature of cyber threats.
What is penetration testing in cyber security?
Penetration testing definition
Penetration testing, often referred to as a simulated cyberattack, is a process designed to evaluate the security robustness of various digital entities—be it an entire system, specific applications, or individual system components. This testing involves simulating the tactics of a cyber attacker, such as attempts to breach API interfaces or internal servers.
What is the primary goal of penetration testing?
The primary goal is to uncover any vulnerabilities that might be present. Not only does pen testing identify weaknesses—it also plays a pivotal role in comprehensive security audits. The insights garnered from a penetration test inform the rectification of detected security gaps, aid in the refinement of security policies, and provide an overall assessment of the current security posture.
And of course, by identifying and addressing vulnerabilities, organizations can significantly enhance their resilience against actual cyber threats, fortifying their defenses in a landscape where security is paramount.
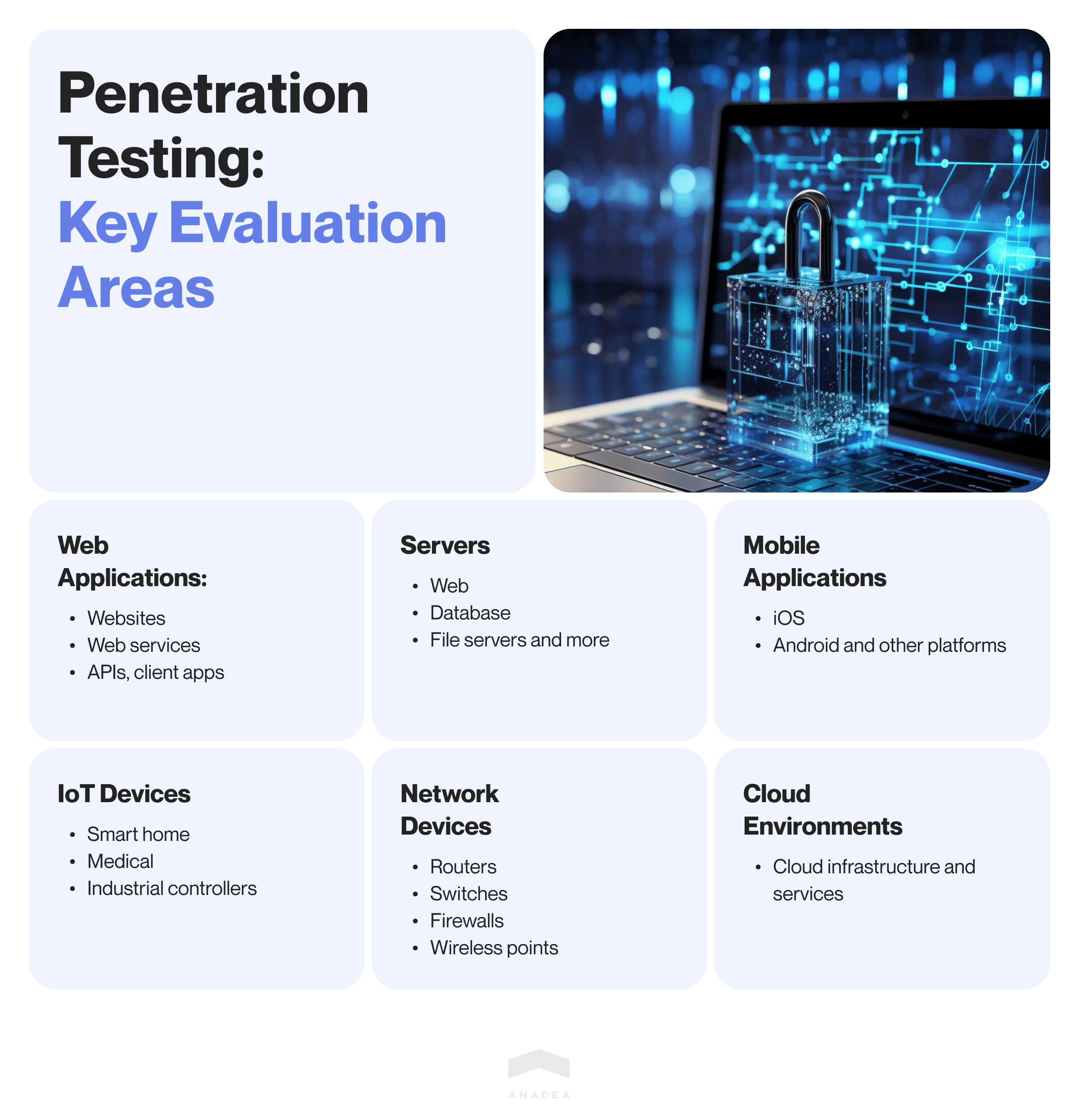
What can be evaluated through penetration testing?
In pen testing, certain key areas are primary targets due to their high vulnerability and critical roles in network and data security. These include:
- Web applications: Websites, web services, APIs, client applications.
- Servers: Web servers, database servers, file servers, etc.
- Mobile applications: iOS, Android, and other mobile platforms.
- IoT devices: Smart home devices, medical devices, industrial controllers.
- Network devices: Routers, switches, firewalls, wireless access points.
- Cloud environments: Assessing security in cloud infrastructure and services to protect hosted data and applications.
Types of penetration testing
Pen testing can be approached from different angles, each with its unique focus and benefits. Let’s explore the key types of pen testing in detail, shedding light on their distinct characteristics and how they can be strategically employed to fortify cybersecurity defenses.
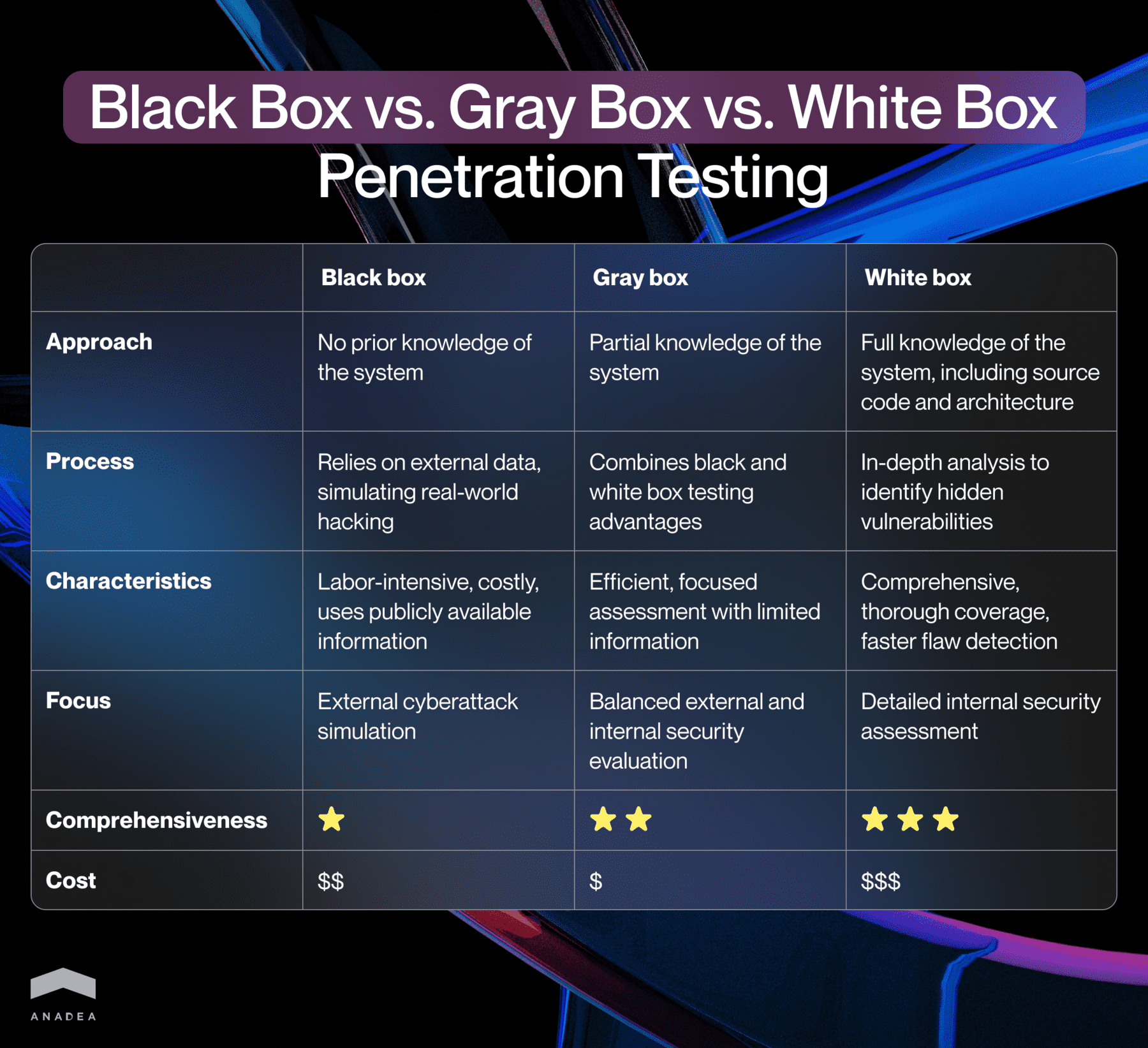
Black box testing
This methodology epitomizes testing in real-world conditions. The tester (‘hacker’) has no prior knowledge of the system’s internal structure—they rely solely on external data inputs for executing attacks. The pen tester operates with a blank slate, akin to an external hacker, and must engage in extensive information gathering and research.
This approach meticulously simulates an actual hacking scenario, leveraging publicly available information such as domains and IP addresses. Despite its realism, black box testing is recognized for being both labor-intensive and costly, reflecting the challenges inherent in external cyberattacks.
White box testing
In stark contrast to black box testing, white box testing (structural testing) involves a comprehensive understanding of the system, including access to source code, architecture, and documentation. This depth of insight facilitates a more thorough analysis and identification of vulnerabilities that might elude black box methodologies.
Pen testers are furnished with complete information about the infrastructure and product upfront, which accelerates the detection of security flaws. The key advantage of this approach is its thorough coverage, as testers are well-informed about the elements that require rigorous testing.
Gray box testing
This type of pen testing strikes a balance by providing the tester with partial knowledge of the system, often including accounts of unprivileged users. It melds the advantages of both black and white box testing, offering a more efficient testing process. Typically, the tester possesses limited information, enabling a more focused assessment than black box testing but without the exhaustive detail of white box testing.
Gray box testing is particularly advantageous when initial black box efforts on a well-secured system reveal the need for some prior knowledge to conduct an exhaustive evaluation. It’s a strategic choice for security assessments that demand both external and internal perspectives.
The penetration testing process
The pen testing process typically unfolds through several distinct stages, each serving a unique purpose. From the initial planning and reconnaissance, which lays the groundwork for the test, to the final analysis, every step is crucial.
- Planning and reconnaissance: This initial phase is pivotal for establishing a structured approach to the penetration test. It involves meticulously defining the scope, objectives, and specific methodologies to be employed. Critical in this stage is the gathering of intelligence to gain a comprehensive understanding of the target’s operational framework and its inherent vulnerabilities. This foundational knowledge is instrumental in tailoring the penetration testing to the unique contours of the system under scrutiny.
- Gaining access (Exploitation): This stage sees the deployment of a variety of sophisticated attack strategies, with common techniques including Cross-Site Scripting (XSS), SQL Injection (SQLi), and the exploitation of backdoors. These methods align with prevalent vulnerabilities as identified in the OWASP Top 10 and CWE Top 25. The objective here is to exploit discovered vulnerabilities to gauge potential damages, which may encompass privilege escalation, data exfiltration, and traffic interception, among others. This phase simulates real-world cyberattack scenarios, providing a realistic assessment of damage potential.
- Access preservation: In this phase, the focus shifts to maintaining access within the exploited system. This is akin to simulating Advanced Persistent Threats (APTs), where the goal is to establish a continuous presence within the system. This allows for the hypothetical exfiltration of highly sensitive data, further mimicking the actions and objectives of sophisticated cyber adversaries.
- Analysis: The culmination of the penetration test is a comprehensive analysis phase. Here, the results of the testing are meticulously compiled into a detailed report. This report elucidates the specific vulnerabilities that were successfully exploited, the nature of the confidential data accessed, and provides a holistic view of the system’s security posture. This analysis is crucial for informing future security strategies and mitigating identified vulnerabilities, thereby enhancing the overall resilience of the system against potential cyber threats.

Strengths and potential weaknesses of penetration testing
Pen testing stands as a vital tool, yet no method is infallible. While offering significant strengths in identifying and addressing security vulnerabilities, it also comes with challenges. Recognizing both the strengths and potential weaknesses is crucial for a balanced understanding and effective implementation.
Where pen testing truly shines
- Proactive vulnerability identification: Penetration testing enables the detection and rectification of security flaws before they can be exploited by cyber attackers. This foresight is instrumental in continuous risk management and threat mitigation.
- Enhanced trust and confidence: Conducting penetration tests demonstrates a company’s commitment to security, thereby bolstering customer confidence and trust in the company’s products and services.
- Refinement of development processes: The insights gained from software penetration testing can be pivotal in enhancing both product quality and the overall development process, leading to more secure and robust products.
Where it is falling behind
- Risk of exposure to third parties: Engaging in penetration testing entails revealing system vulnerabilities to external entities. It’s crucial to ensure complete trust in the testing partner to avoid any potential misuse of sensitive information or concealment of critical vulnerabilities.
- Potential for inaccurate results: While comprehensive pen testing service offers numerous benefits, it may not always be a feasible option due to financial constraints. Beyond that, the effectiveness of the testing is contingent upon the optimal utilization of the results. Insufficient testing or inadequate response to findings can lead to a false sense of security, undermining the overall objective of the exercise. The solution? Implement a structured approach to address and follow up on the findings, ensuring that all identified issues are resolved effectively.

Manual or automated penetration testing?
Choices don’t end there. In addition to the concerns above, organizations often face a dilemma—whether to opt for manual or automated penetration testing. This is why one needs to discern the fundamental differences between these two types of penetration tests, as each carries its distinct set of advantages and challenges.
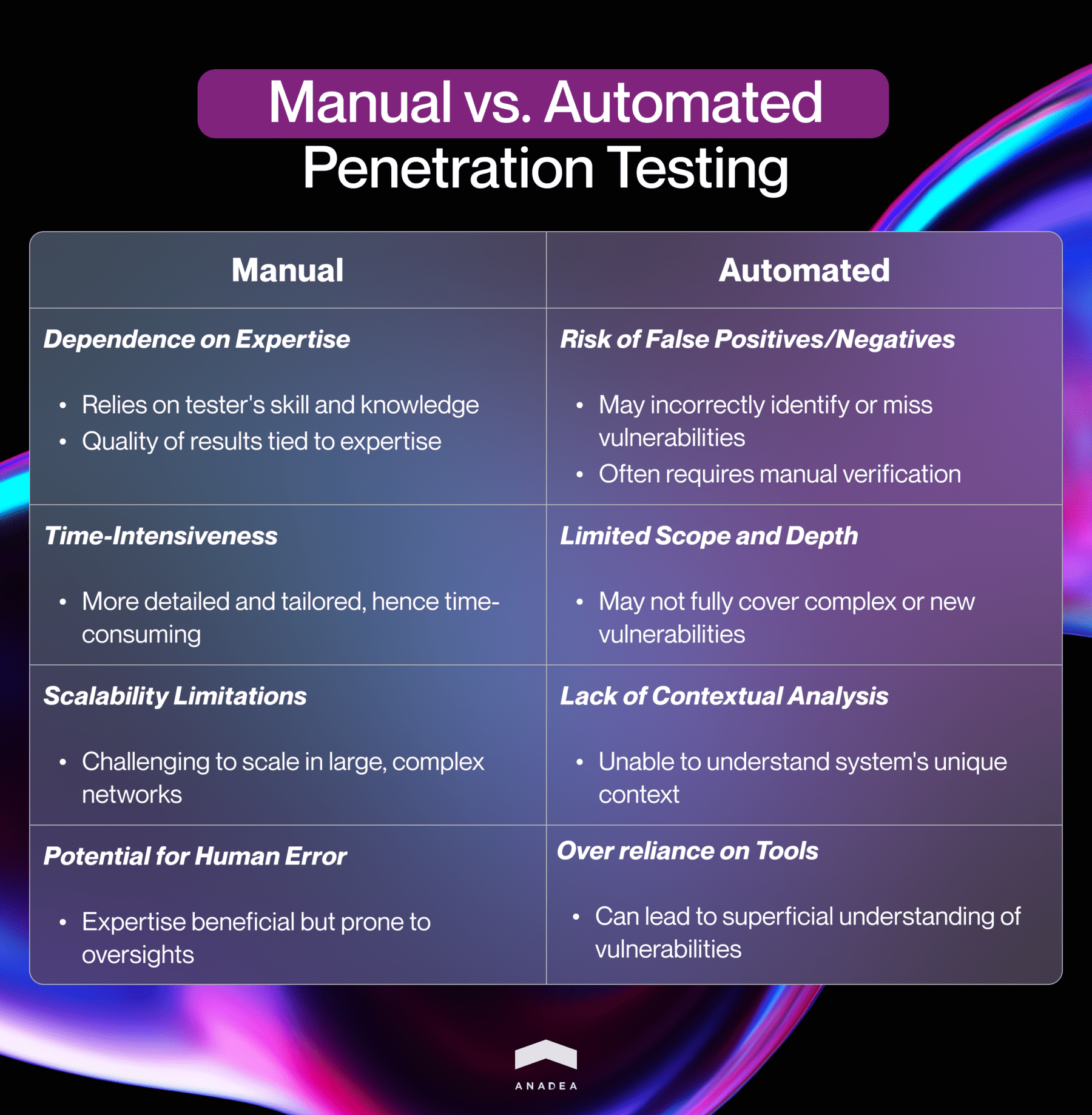
Specifics of manual penetration testing
- Expertise dependency: Relies heavily on the skill and knowledge of the cybersecurity professionals conducting the test, making the quality of results contingent on their expertise.
- Time-intensiveness: Manual testing is often more time-consuming due to the detailed and tailored approach required for each test scenario.
- Scalability limitations: Difficult to scale across large and complex networks or applications due to the labor-intensive nature of the process.
- Potential for human error: While expertise is a strength, human error can also influence the results, leading to possible oversights or misinterpretations.
Specifics of automated penetration testing
- Risk of false positives/negatives: Automated tools may incorrectly identify vulnerabilities (false positives) or miss existing vulnerabilities (false negatives), requiring additional manual verification.
- Limited scope and depth: Automated tests may not adequately cover complex, customized, or new types of vulnerabilities, as they typically follow predefined patterns.
- Lack of contextual analysis: Automated systems lack the ability to understand the unique context of a system, potentially overlooking nuanced vulnerabilities.
- Over-reliance on tools: Sole dependence on automated testing can lead to a lack of in-depth understanding of the vulnerabilities and their potential impact.
The best of both worlds
Judging by the specifics of both manual and automated pen testing methods, it comes as no surprise that a balanced combination of both approaches is the most effective strategy. Employing professional tools under the guidance of skilled specialists can create a testing system that is both flexible and cost-effective, without compromising on efficacy.
Our conclusion? The landscape of software penetration testing is nuanced, requiring a thoughtful approach that matches the needs of each organization. By balancing the strengths of manual and automated, companies can fortify their defenses effectively and efficiently.
Bottom line
As we’ve journeyed through the intricacies of various testing methodologies and the detailed process of identifying vulnerabilities, one thing becomes clear: successful penetration testing is an art as much as it is a science. From the depth of manual testing to the efficiency of automated systems, the balance of methodologies underscores a commitment to robust security.
As we face a digital future, the need for comprehensive cybersecurity is more critical than ever. Embrace the challenge and turn potential vulnerabilities into strengths! Let Anadea’s pen testing expertise be the catalyst for your organization’s enhanced security. Reach out to us, and together, let’s fortify your cyber defenses. Your journey towards a secure digital ecosystem starts here!
Have questions?
- A pen test, short for penetration test, is a strategic process where cybersecurity specialists conduct controlled cyberattacks on an organization’s systems, networks, or applications. This exercise is designed to discover and exploit security vulnerabilities, mirroring the tactics of actual hackers. It serves as an essential tool for proactively strengthening a company’s cybersecurity defenses.
- Cybersecurity experts who know how to perform a pen test are the ones to deliver this service. These professionals possess a deep understanding of network and application vulnerabilities and how malicious attackers exploit them. Their role is to simulate cyber attacks in a controlled environment to identify and help address security weaknesses.
- Penetration testing aims to uncover security vulnerabilities in an organization’s systems, networks, or applications. It involves experts simulating cyberattacks to identify weak spots in security. This process helps organizations understand where they need to bolster their defenses, preventing real hackers from causing damage or accessing sensitive data. Essentially, it’s a proactive measure to enhance cybersecurity and safeguard digital assets.
- Penetration testing helps identify and fix security gaps before they can be exploited by malicious attackers. It acts as a preemptive defense against cyber threats, protecting sensitive data and maintaining the integrity of an organization’s digital infrastructure. It’s vital for ensuring compliance with security standards and preserving customer trust. By highlighting security weaknesses, penetration testing enables organizations to make meaningful improvements to their cybersecurity strategies.
Don't want to miss anything?
Subscribe and get stories like these right into your inbox.
Keep reading

PHP or Golang: How to Choose the Right Language for Web Development in 2025
Discover the differences between Golang and PHP to choose the right language for your project. Compare performance, scalability and typical use cases to make a decision.

AI in asset management: Trends to watch out for in 2025
Read our article to find out how you can efficiently implement AI in asset management to leverage the biggest benefits for your business.

How to create an investment app: Guide 2025
Planning to launch an investment application? It can be a very promising idea in 2025. Read our investment app development guide to launch a successful product.
Contact us
Let's explore how our expertise can help you achieve your goals! Drop us a line, and we'll get back to you shortly.